Spoiler alert; the answer is yes. And by quite a bit. But with reservations. You have to look at the whole picture.
I took an example linked AWS account that had two Windows EC2 compute instances currently running. Both are webservers, one for production and one for staging. The following monthly cost comparisons use both on demand and savings plans that are for 1-year commitments with no down payment as this is typical for me.
| AWS Instance | On Demand | Savings Plan | Azure Instance | On Demand | Savings Plan |
| t3a.2xlarge | $327 | $266 | B8ms | $247 | $171 |
| m7i-flex.2xlarge | $535 | $461 | D8d v5 | $330 | $226 |
As you can see, I could potentially be saving up to $330 on just these two instances by moving to Azure from AWS. $3,960/yr is a decent vacation or maybe a paycheck. So why not switch cloud providers? Well, there is the cost of learning a new infrastructure and dealing with all the nuances that come with it. But in this specific case, it’s managed database services.
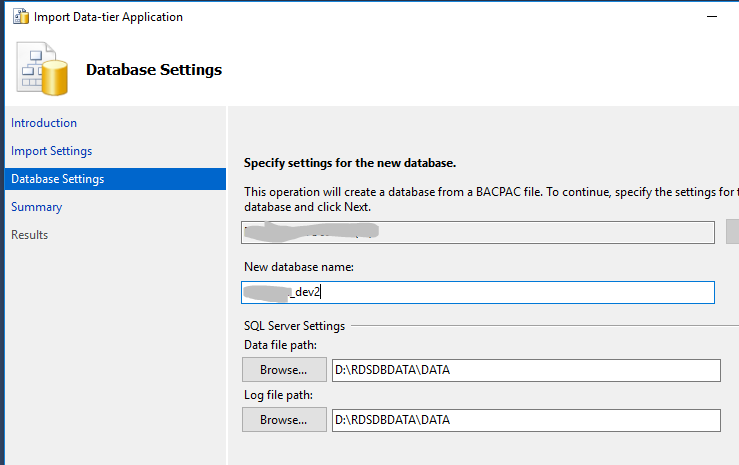
The following compares single AZ Microsoft SQL Server Web Edition on Amazon RDS with Provisioned vCore Azure SQL Database. Note that Azure SQL Database is edition agnostic. There is also Azure managed SQL, but that’s even more expensive. We won’t be comparing AWS reserved instances to Azure reserved instances because we may never buy a reserved RDS instance on AWS for this account. Once you buy it, you are very locked in. No instance type or size exchanges, nor selling it on a marketplace. But you can see, a reserved instance on Azure is still more expensive than AWS on demand.
| AWS Instance | On Demand | Azure Instance | On Demand | Reserved Capacity |
| db.m6i.xlarge | $430 | D4s v5 | $737 | $581 |
| db.m6i.2xlarge | $890 | D8s v5 | $1,105 | $1,162 |
Find that odd? You actually get a better value on Azure when comparing it to the standard or enterprise edition. However, I deal primarily with Web and Express editions. The majority of applications I handle don’t require the functionality or redundancy built into standard and enterprise editions. However, if you were to require standard or enterprise, I would strongly suggest looking at using Azure to save you quite a bit of money, or start using Linux and an alternative database technology like Aurora on AWS.
When we factor in the managed database, we now do not find value moving to Azure from AWS as the realized savings is now lost. Yes there are options to spin up the database on a VM and manage it ourselves, but now you are adding in monthly labor costs and additional license costs for backups, not to mention the lost performance gains RDS or Azure SQL Database brings.
In conclusion, hosting Windows servers on Azure over AWS can save you money. But you need to factor in all the services, even beyond the database, including system administration labor and 3rd parties utility integration. Why can Azure have potentially significant savings on Windows servers? Because Microsoft owns both the infrastructure and the licenses. They do not translate the same license discounts to other cloud providers. For example, you used to be able to bring your own SQL license to AWS RDS, but that was discontinued some time ago.
Note: Turn off the “Azure Hybrid Benefit” slider when viewing Azure pricing. This option requires bringing your own license and does not facilitate an accurate pricing comparison.
If you are interested, Microsoft has an official AWS-to-Azure compute mapping guide; however, I used Microsoft Copilot to help me find the equivalent instance types and sizes. There are also web utilities that map them you can search for.




 I’ve taken the courses, I have practical experience, I paid the exam fee and I past the test. That makes me an “Amazon Web Services (AWS) Certified Solutions Architect – Associate”. Wow what a mouthful, but what does that mean to you?
I’ve taken the courses, I have practical experience, I paid the exam fee and I past the test. That makes me an “Amazon Web Services (AWS) Certified Solutions Architect – Associate”. Wow what a mouthful, but what does that mean to you?